The Challenge
It is unfortunate, but in today’s digital world, every business no matter on size, sector or location is vulnerable to cyber-attacks. Therefore putting layers of protection in place backed by some sensible policies will make sure you are not the easy target. However there is a fine line between the right level of security and becoming overprotective and implementing ‘business disablers’, after all, we all still need to be able to do our work and keep our customers happy while being as secure as possible.
The Solution
Using NJC to implement Cyber Essentials will offer you a reasonable level of protection and ensure you are not an easy target; we will achieve the result in a very cost-effective and timely manner. We will work with your existing in-house IT or your external provider to secure your systems to provide you with the best starting point possible for cyber-attack protection.
What we do differently
We are always looking to be different from others, providing extra value to our customers. We will also let your IT people know of any new threats and advise on how to add additional protection for your systems when necessary.
A significant area of any Cyber defence is the human element, so we can provide training events and materials to enable your staff to spot the potential issues before they cause a problem.
A major area of any Cyber defence is the human element, you will be given early access to training events and material provided by us to ensure you keep your human side of cyber protection fully informed and trained on sporting potential issues before they arise, and when they do happen knowing how to respond to limit the impact on the business.
Why use us?
Since 2002 NJC has been providing IT services to companies of all sizes. In 2017 we moved into cyber-security side of IT, after more than 15 years of our customers not being compromised we felt this was a natural move. We want to share our experience and best practice with everyone.


The Benefits of a Cyber Essentials Certification
Show commitment to security
To win public sector work
Competitive advantage
Safeguard commercially sensitive data
Attract new business
Gain independently verified accreditation
Protect your company’s profits and reputation
Clear system view
%
Of Breaches are due to weak or stolen passwords
%
of businesses have a formal policy that covers cyber security risks
%
of businesses have spent money on their cyber security, most of it after a breach!
%
of breaches are related to staff receiving fraudulent emails
The 5 Steps to Cyber Protection
Firewall
User Access Control
Secure Client Configuration
Virus and Malware Protection
Patch Management
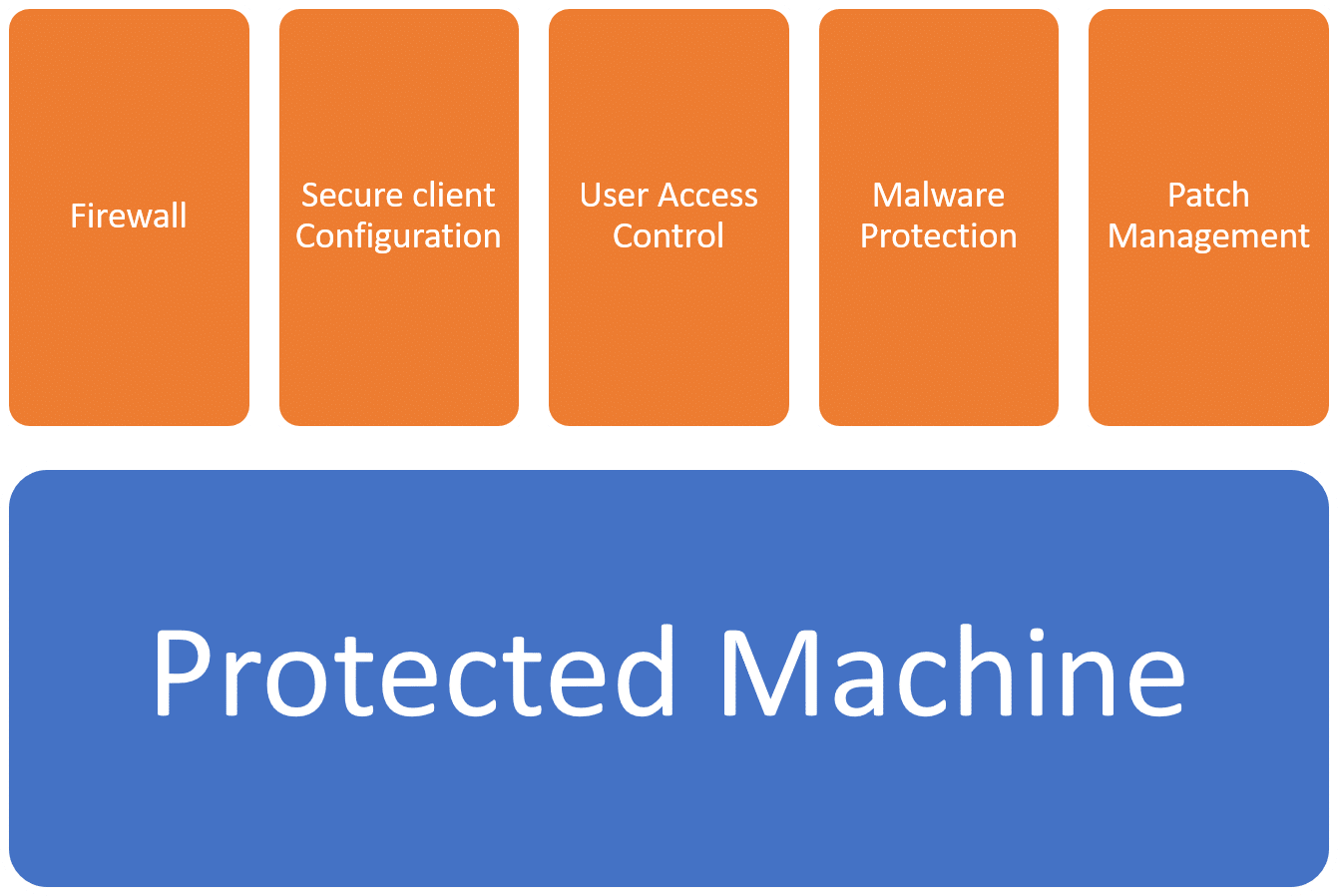
Our experience is that most businesses have these steps in place already, some are better than others but formalising these as part of your Cyber Policy will provide a better level of protection.
The most common types of breaches
- staff receiving fraudulent emails 72%
- viruses, spyware and malware 33%
- people impersonating the organisation in emails 27%
- Ransomware 17%
Pricing options
a question you’d like answered or would just
like an informal chat, contact us.
